Exchange is a very powerful piece of software. Unfortunately, misconfigurations, shared mailbox access, rogue admins and more can allow sensitive data to be viewed or deleted.
I experienced this a few weeks ago where a member of a shared mailbox was deleting emails that needed dealing with! Let’s have a look at how to track down the culprit in this example.
With Exchange email services playing a huge part in information transfer today, it is important to keep an eye on exactly what is happening on your servers… but what happens when your servers are no longer just in your datacentre? Hybrid Exchange configurations complicate auditing with more points to check. You can use Netwrix Office 365 Exchange Online Auditing to help investigate what’s going on without you realising!
Here, we’re dealing with an Exchange 2013 hybrid configuration in partnership with an Office 365 subscription. The shared mailbox in question was located on one of the on-premise servers.
On-Premise Mailboxes
The first thing we had to do to track this user down was to turn on mailbox auditing. Unfortunately, we hadn’t previously enabled this – not had a reason to!
In your configuration, you can enable it either per-mailbox, or for all mailboxes:
#single mailbox
Get-Mailbox ‘identity | Set-Mailbox -AuditEnabled $True#all mailboxes
Get-Mailbox -Filter {(RecipientTypeDetails -eq ‘UserMailbox’)} | foreach {Set-Mailbox $_.Identity -AuditEnabled $True}
Once you’ve done that you can optionally set the audit information you want recorded. The default in Exchange 2013 is:

Which translates as:
- Keep the audit information for 90 days
- Record when admin users: change a message (ie marked it as read/unread), copy/move to a folder (including deleted items), delete it, permanently delete it, export data to PST, create or send a message
- Record when delegated users: change messages, (permanently) delete, create new messages or send them
You can change this if required:
Get-Mailbox ‘identity’ | Set-Mailbox -AuditAdmin List of audit types -AuditDelegate List of audit types -AuditOwner List of audit types -AuditLogAgeLimit Number of days to keep data
The only time I would personally use this is to set SoftDelete, HardDelete for AuditOwner (to track if a user is deleting messages to say they didn’t receive them for example).
Bear in mind that when you issue this command it overwrites anything already set for that mailbox.
If you’ve just enabled Auditing, be aware that it will only record events from now on. For me, it was a waiting game to see if the user would login again.
Now you can search the audit log using the following command:
Search-MailboxAuditLog ‘identity’ -ShowDetails -StartDate (get-date).AddHours(-1) | fl
Here, I knew the activity took place in the last hour, so I’m specifying -startdate with a timespan of an hour ago. I ran the command and… nothing. No results.
After some digging I remembered that users part of the ‘Domain Admins’ group (ie my current user) aren’t in the ‘Records Management’ role of Exchange 2013 and higher by default.
Add-RoleGroupMember ‘Records Management’ -Member ‘identity’
I gave myself that role, waited a few minutes and then re-ran the command, and: (Record adapted slightly to protect the innocent!)
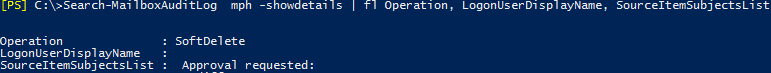
As you can see I used a slightly different version of the command to just show the details I’m interested in – what happened, who did it and to which email.
In our case, the person deleting the messages was actually doing it without realising what was happening – one of the many problems with shared mailboxes!
Auditing Remote Mailboxes
The workflow for this process is pretty much the same for remote mailboxes, you just have to connect to the Exchange Online instance using this PowerShell command first:
$creds = Get-Credential
$eonlinesession = New-PSSession – ConfigurationName Microsoft.Exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $creds -Authentication Basic -AllowRedirection
Import-PsSession $eonlinesession
Check you’ve connected successfully by issuing something like get-mailbox and see if it returns mailboxes that you know are offsite:
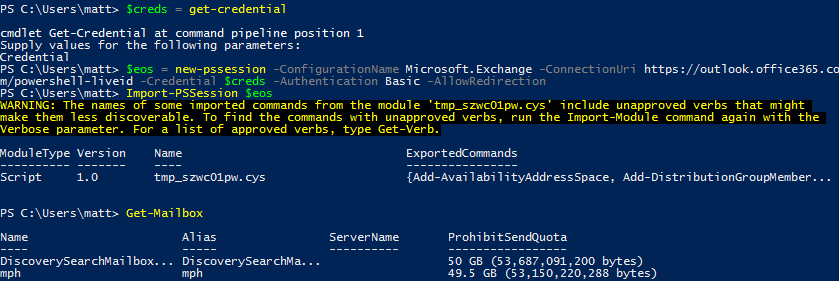
Once you’ve finished, don’t forget to disconnect otherwise you could run into issues where you use all the concurrent PowerShell sessions for your user up and have to wait for them to timeout.
Remove-PsSession $eonlinesession
Taking it further
Exchange auditing is very powerful – you can audit things right down to how many times a mailbox was logged into by an owner.
Couple of extra things to bear in mind:
- You can also access the auditing interface via Exchange Control Panel (go to outlook web access and change the url to /ecp).
- Mailbox auditing information is stored in the user’s mailbox in a hidden folder. If you audit too much info, it does increase the size of their mailbox!