I recently took on a new client who was having problems with a server on their site. They have a 1gbps dedicated connection to the Internet that was being saturated by an incoming DDoS attack.
Opening Resource Monitor on their gateway yielded some interesting results – there were thousands of DNS queries being performed per second for several websites.
Looking in the services for the gateway, it had been setup as a secondary DNS server, slaved to a Active Directory GC (Global Catalog – yes, American Spelling!). I temporarily stopped the DNS service using PowerShell:
stop-service DNS
Sure enough, within 30 seconds or so, the connection was back to normal utilisation. Starting the service again saturated the connection.
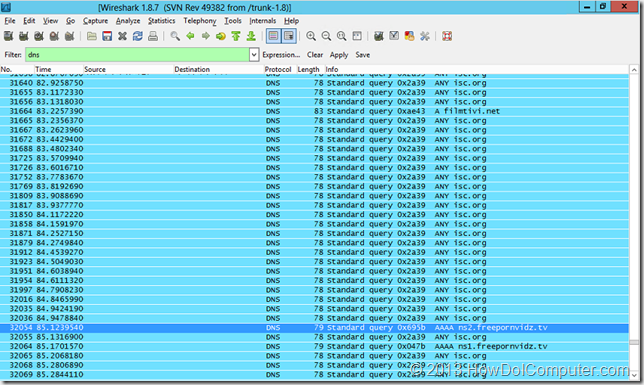
Wanting to find out exactly what was going on, I downloaded the Wireshark packet sniffer utility and set it running. Here’s what I saw:
As you can see, there’s many requests for porn sites and for some reason, the Internet Systems Consortium!
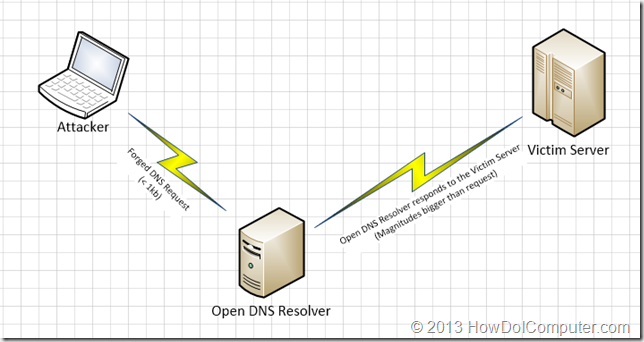
This is known as a DNS Amplification, Reflection or Recursion Attack (for background reading check here and here), where the basic idea is that an attacker uses your server’s DNS system to bombard a victim with unwanted DNS traffic. See beautiful Visio diagram below:
The basic flow is:
1. Attacker sends a relatively small DNS query to the DNS server asking for all the DNS records for a target. For example:
2. The DNS server with recursion enabled goes and asks its parent server for the records. This returns a response much larger (see for yourself using an online DIG tool)
3. Because the original DNS request was send using UDP which doesn’t require an acknowledgement, it can be forged to look like it came from a different IP (the victim server).
4. DNS server passes response to the victim server, so in effect your server becomes the DoS attacker.
5. The attacker can send thousands of requests to many servers at once until target is offline.
The recommended guidance (Microsoft) for this situation is that you disable recursion on your DNS server. Unfortunately, this also disables forwarding and any queries that your DNS server cannot resolve itself (ie if one of your network clients asks for a website IP, the server will just say ‘I don’t know, sorry’.
Normally, you only want your DNS server to answer queries for your local network – there are a couple of ways of doing this:
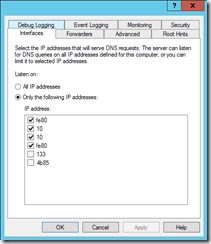
- If you have multiple network cards or IPs configured, check that the DNS server is only listening on private addresses.
- Or, you can setup a firewall rule to only allow DNS queries from IPs within your subnet or LAN.
I did both of these on the gateway server just for good measure, but left recursion enabled so that internal clients can still resolve outside of the scope of the server.